Settings for Flatpak sandboxing for the Zoom Linux client
Why
Zoom is the video conferencing solution we currently (summer term 2020) use at JKU Linz for remote teaching while on-premise hosted solutions are being evaluted. While participants in a video meeting can use a sufficiently up-to-date web browser to join, hosting and controlling advanced options (as well as upcoming E2EE support) require the native Zoom client to be installed. Unfortunately, the Zoom client has a bad security track record (e.g. just 14 days ago with a Windows client 0day, RCE in June, login credential leaks in April, forced join - even after uninstalling the client - last year, etc.).
How
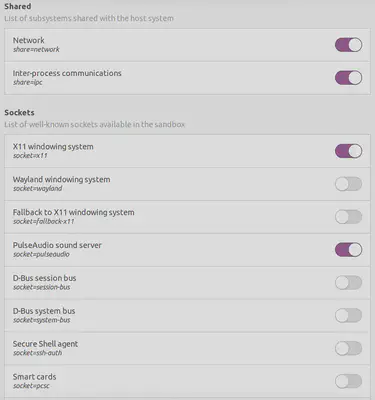
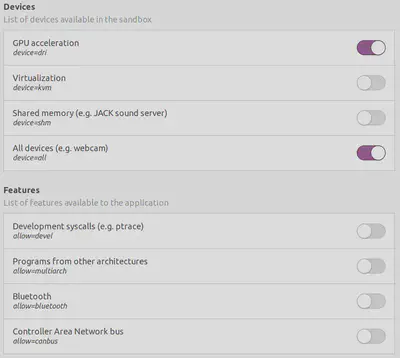
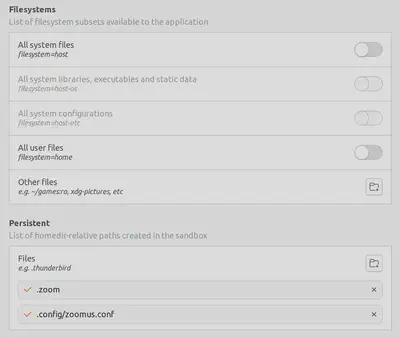
Flatpak is a new-ish package format for Linux desktop applications and natively supports sandboxing. Zoom is also available as a Flatpak package from the official flathub repository. Installing this version instead of the native client from Zoom itself supports setting permissions locally. After some tweaking - and explicitly denying access to the whole user directory - I use the following overrides (in .local/share/flatpak/overrides/us.zoom.Zoom):
[Context]
devices=dri
filesystems=!home
persistent=.config/zoomus.conf;.zoom
In Flatseal, my config looks like this: